There is a reason you almost always see phishing as a part of security awareness training. It has been the primary method of online attack over the past decade or two. Phishing emails are used to initiate ransomware, credential theft, data breaches and more. In an effort to keep you protected, learn how the SLAM approach can help detect phishing.
What Is The SLAM Method in Cybersecurity?
The SLAM method in cybersecurity is a structured approach to identifying phishing emails and other social engineering attacks. The acronym SLAM stands for Sender, Links, Attachments, and Message.
It provides a practical framework for remote workers and others to evaluate emails critically before taking action, reducing the risk of falling victim to malicious attempts to steal sensitive information or compromise systems.
You might be wondering why phishing is still such a serious concern. It’s because phishing still works. These scams evolve as the technology changes. For instance, AI technology making it easier to pinpoint targets for these scammers.
If these phishing techniques stop working, the scammers will just switch to a different type of attack. But, for now that hasn’t happened. People are falling victim to phishing scams everyday. They are tricked into opening malicious emails with unsafe URLs and attachments, all to gain passwords and other login credentials.
Studies show that after the 6 month mark of cyber training, an employees ability to detect phishing begin to decline. They start forgetting what they’ve learned, which always negatively affects cybersecurity.
That’s why we put together the SLAM technique. To help your staff remember how to identify phishing.
Employees can use SLAM as a checklist when receiving questionable emails. It makes remembering what to look for much easier. They are able to avoid overlooking something important. All they have to do is check off the acronyms cues.
Verify the Sender
The first thing you should ALWAYS check is the sender of the email. Scammers love to use look-alike email addresses or a counterfeit email address. It can be easy to mistake a fake address for the real one.
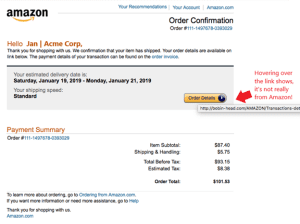
Let’s look at an example of a phishing email domain.
“@local.bankofamerica.com”
The scammers are trying to trick you into believing you received an email from Bank of America. When actuality you haven’t. They use the legitimate URL inside a fake one.
They will also send you a very persuasive email. Lot’s of commonly seen visuals and wording. Emails like that trick a lot of people into divulging their personal details. If you don’t verify the sender, these emails can look perfectly normal. Scammers acting as a bank trying to get you to apply for a credit card can easily get you to turn over your social security number, income and other personal information.
An easy tip is to type the email address into google. You will quickly reveal if that domain is behind other scams.
Hover Over Links Instead of Clicking
It’s common practice for emails to include hyperlinks. Often, they are able to bypass antivirus and anti-malware detection. These filters scan files for malware-containing attachments. However, a link to a risky website might not contain dangerous code.
In an email, links can take the form of hyperlinked text, graphics, and buttons. It’s important to hover over links without clicking on them in order to see their actual URLs. This frequently can identify a phony email scam right away.
If you are checking emails on your mobile device, this may be a little tricky. If you are in a situation without a mouse, it’s best to avoid clicking the URL at all. Visit the alleged website instead to verify the accuracy to the message.
Never Open Unexpected or Strange Attachments
Scammers still like to use file attachments in their phishing emails. The messaging on the email will try very hard to get you to open the attachment. They will use familiar words and document titles to get you to click without thinking too much into it.
It’s hard to determine which file types to avoid opening. Cybercriminals are skilled at introducing malware into all different kinds of documents. Even some PDFs have been known to contain viruses.
Never open a file attachment that seems odd or unexpected. Scan all attachments with an antivirus/anti-malware program before opening.
Carefully Read the Messaging
We have gotten really good at scanning through emails. This skill helps to quickly move a long the constant new information we receive daily. However, if you mistakenly skim through a phishing email, you can miss several obvious red flags.
Look at the phishing illustration that was presented in the “Links” section above. The second sentence contains a minor grammatical mistake. Did you catch it?
Instead of saying “We confirm that your item has shipped,” it reads “We confirmation that your item has sent.” Although they might be challenging to see, these mistakes are a huge giveaway that the email is not authentic.
Get Support Fighting Phishing Attacks
We hope you can see how the SLAM approach can help detect phishing. Defenses against phishing attacks can overall be strengthened by security software and awareness training alike. To discuss your needs for email security, contact us today.
What to Do When You Recognize a Phishing Email
Do NOT Interact with the Email
Avoid clicking any links, downloading attachments, or replying to the email. Interaction with malicious content could install malware, ransomware, or lead to credential theft. For example, even hovering over a link in some email clients might trigger tracking mechanisms. Instead, mark the email as suspicious in your mind and proceed to the next steps without engaging further.
Report the Email to Your IT or Security Team
Immediately notify your organization’s IT department or cybersecurity team, following their established reporting protocol. Most companies have a designated email address (e.g., [email protected]) or a ticketing system for reporting phishing attempts.
Provide details such as the sender’s email address, subject line, and any suspicious elements identified using the SLAM method. This allows your team to investigate, block the sender, and alert others if necessary.
Mark the Email as Spam or Phishing
Use your email client’s built-in features to flag the email as spam or phishing. For instance, in Gmail, click the “Report phishing” option, or in Outlook, select “Report Message” as phishing. This action helps train the email provider’s filters to better detect similar threats and moves the email to a spam or junk folder, reducing the chance of accidental interaction.
Delete the Email Safely
After reporting, delete the phishing email from your inbox to prevent accidental clicks, especially if you’re working in a busy remote environment. If your email client allows, move it to the “Deleted Items” folder and then permanently delete it.
Avoid opening the email again to review its contents unless instructed by your IT team, as this could expose you to risks.
Verify and Monitor Your Accounts
If you suspect you may have interacted with the email before recognizing it as phishing (e.g., clicked a link or entered credentials), immediately contact your IT team for assistance.
Change any potentially compromised passwords from a secure device, enable two-factor authentication (if not already active), and monitor your accounts for unusual activity. For example, check for unauthorized logins or unexpected emails sent from your account.
Educate Your Team
Share the experience with colleagues (without forwarding the phishing email directly) to raise awareness. For instance, mention the red flags you noticed, such as a suspicious sender domain or urgent language, as identified through the SLAM method.
If your organization offers phishing awareness training, encourage participation to strengthen collective defenses, especially for remote workers who may face similar threats.
If you’d like to find out more about what’s new in the tech world, make sure to follow our blog!
Click here to schedule a free 15-minute meeting with Stan Kats, our Founder, and Chief Technologist.
STG IT Consulting Group proudly provides IT Service in Greater Los Angeles and the surrounding areas for all of your IT needs.
Ready to Get Started?
Let’s dive into your IT!
Schedule a free 15-minute Virtual Meeting with a Business Technology Specialist of STG Infotech and get a closer look into your IT challenges.
We will assess your current IT infrastructure and answer any questions you may have about IT Services or partnering with STG IT.




